ISO 27001 Starter Kit
Looking for a Clear Roadmap to ISO 27001?
Simplify your path to ISO 27001 with a customizable project plan, process maps and supporting resources.
See it in Action
What You’ll Get
Let Me Show You ALL the Resources You'll Get Access to When You Get the ISO 27001 Starter Kit Today.
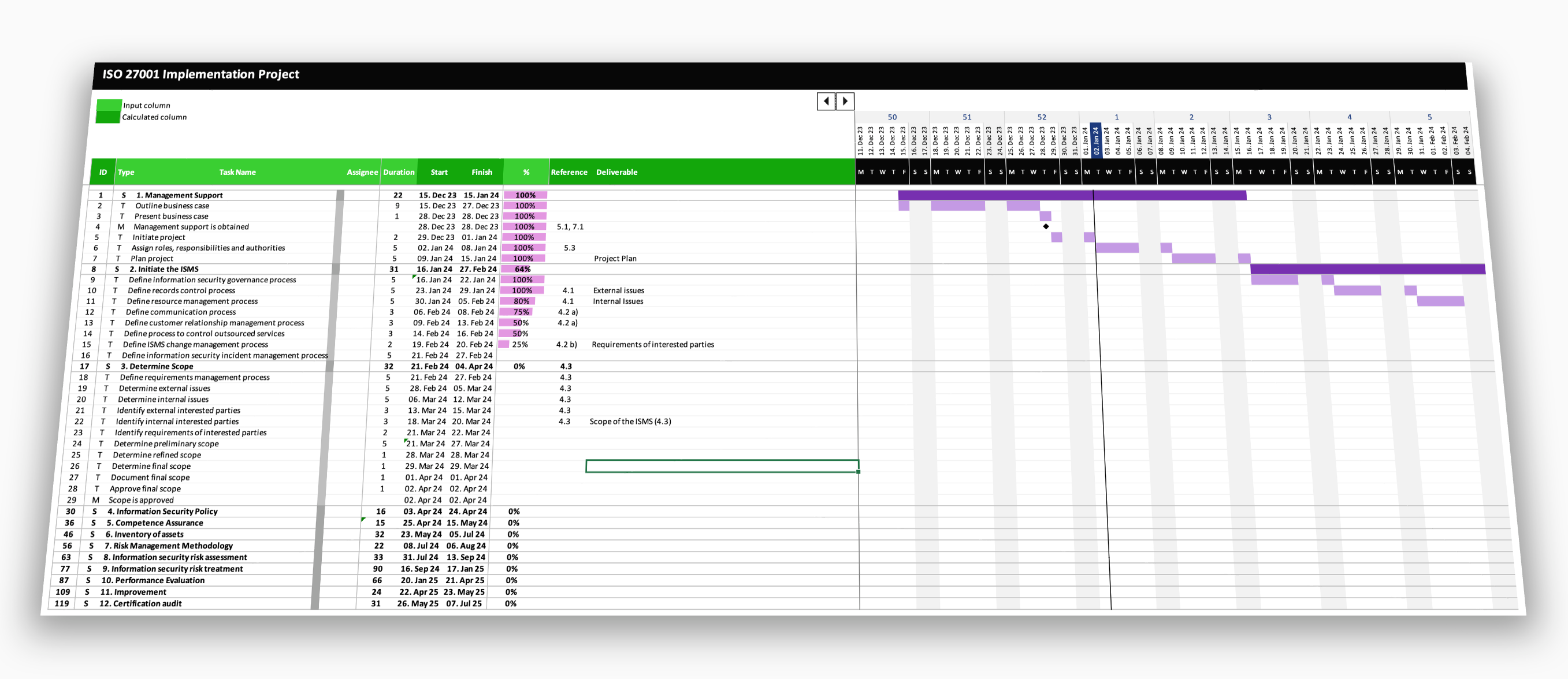
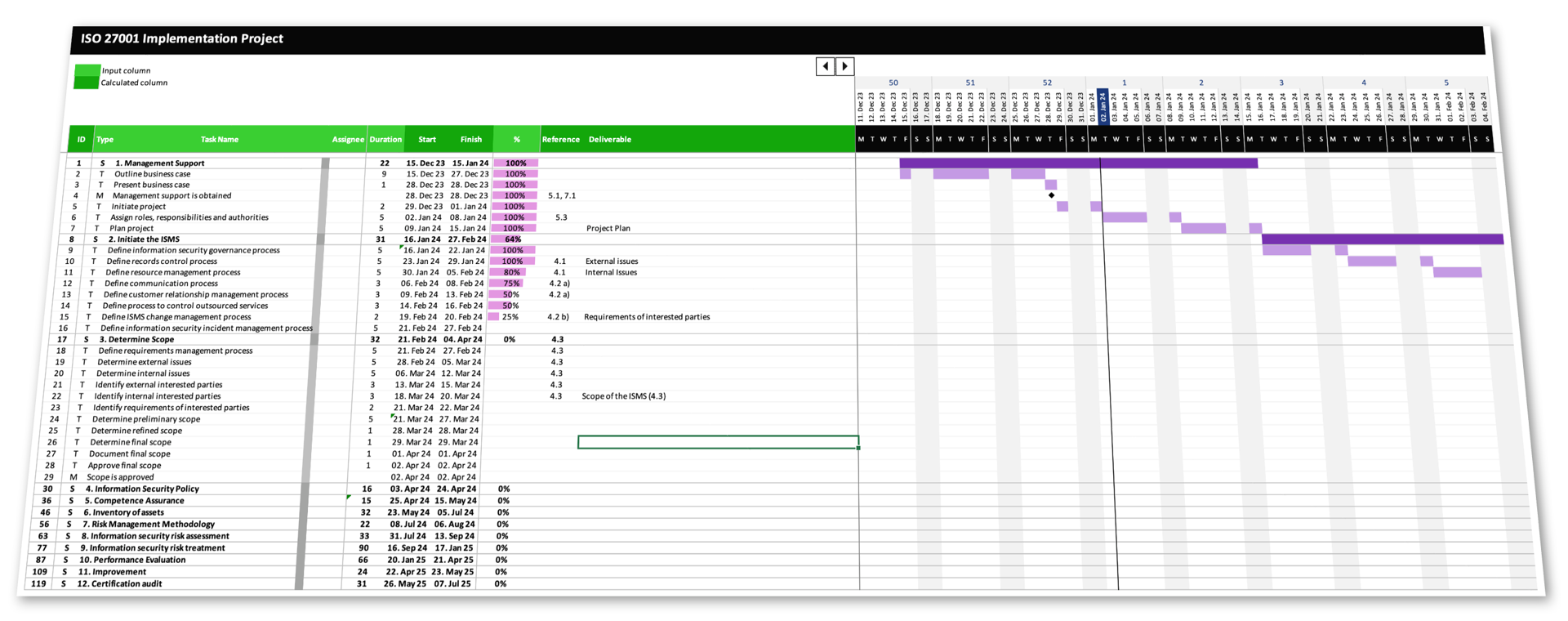
Project Plan
The Starter Kit features a fully customizable project plan for the implementation of an ISMS in accordance to ISO 27001.
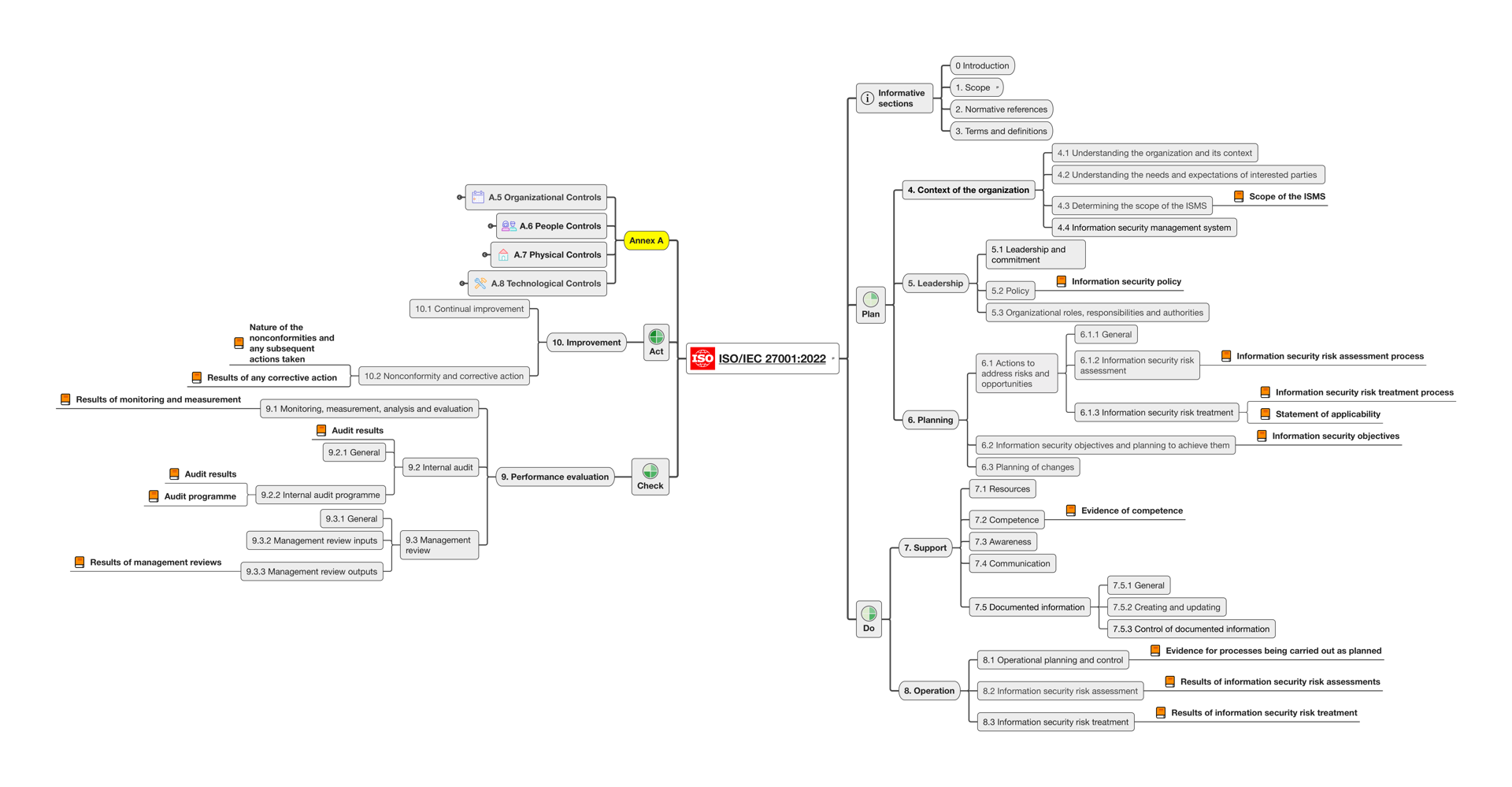
Mind Map Collection
Standards can be confusing and tiring. Visuals make understanding the requirements fast and enjoyable.
18 Process Maps
Adapt the included reference processes to your specific needs, allowing you to operationalise the ISMS right away.
Bonus Resources
Use the provided mapping table to compare the old and new controls and benefit from a comprehensive list of all standards of the ISO 27000 family of standards.
✓ Annex A Control Mapping Table (2013 → 2022)
✓ List of ISO 27000 Family of Standards
A Plan is the Secret to a SUCCESSFUL Implementation Project
Without a Plan
❌ Higher chances of non-compliance
❌ Higher Implementation Costs
❌ Longer Project Duration
❌ Confusion
❌ Reduced confidence among stakeholders
With a Plan
✅ Fast-Track to Compliance
✅ No Trial & Error
✅ Efficient Approach
✅ Less confusion
✅ Confidence among stakeholders
If you’re here right now, I know it’s because of one of the following reasons:
The Challenges You Face
Implementing ISO 27001 is a tough challenge that many people struggle with.
❌ Complexity: ISO 27001 is full of details that can be hard to follow. Risk assessments, statements of applicability – the list of requirements seems endless.
❌ Trial & Error: Without a clear roadmap, organizations are often forced to rely on trial and error. This approach is not only costly but also frustrating and time-consuming.
❌ Time-Consuming: Many organizations find themselves dedicating months to the implementation process. The numerous assessments, documentation, and internal audits required can put a strain on your resources and hinder your day-to-day operations.
❌ Costly: Whether you're considering hiring consultants or assigning a dedicated internal team, the costs associated with ISO 27001 can quickly pile up. From training to necessary tools, the expenses can be hefty.
❌ Generic Nature: ISO 27001 is descriptive and generic, which makes it even more difficult to implement. The one-size-fits-all approach means that you have to interpret the standard and adapt it to your organization's unique context, adding another layer of complexity.
Listen, You are Not alone!
I know how complicated and time consuming a certification journey can be...
The Solution for You
Imagine having a step-by-step blueprint, tailored to fit any organization regardless of size, type, or nature. Imagine having access to a comprehensive collection of resources designed to simplify and accelerate your implementation process.
✅ Clarity: With a structured 12-step approach, the complexities of ISO 27001 are broken down into manageable steps, giving you a clear path forward.
✅ Proven Method: You can avoid the costly and frustrating trial-and-error phase. This project plan is based on a proven 12-step approach that has been successfully implemented by organizations of all sizes and types.
✅ Efficiency: No more lengthy implementation processes. You'll have access to a proven blueprint designed to save you hundreds of hours.
✅ Affordability: You can now get closer to compliance without the exorbitant costs. The ISO 27001 Lead Implementer course offers a growing collection of resources at a fraction of the price.
✅ Personalized Approach: With a plan that translates the generic contents of ISO 27001 into actionable advice, you'll have a personalized roadmap, tailored to fit your organization's unique context.
The Plan
Structure
Step 1
🤝 Management Support
Secure the backing you need to successfully implement ISO 27001 by gaining the endorsement and commitment of your organization's leadership.
Step 3
🔳 Determine Scope
Define the boundaries of your ISO 27001 implementation by identifying the parts of your organization, the information, and the systems that will be included.
Step 3
🔳 Gap Analysis
Design and establish the necessary management, core and support processes to ensure the ISMS can deliver its intended results.
Step 4
🔐 Define Information Security Policy
Establish a strong foundation for your information security management system by creating a policy that outlines your organization's security objectives and commitments.
Step 5
👩🏫 Competence Assurance
Enhance your information security by assessing, developing, and documenting the competence of personnel, ensuring they meet the necessary security standards and objectives.
Step 6
📦 Asset Inventory
Get a clear view of what needs to be protected by cataloging all the information assets within the scope of your ISO 27001 implementation.
Step 7
📊 Risk Management Methodology
Choose a risk management methodology that fits your organization, ensuring you can effectively identify and evaluate the security risks that threaten your information assets.
Step 8
🔍 Risk Assessment
Gain insight into the potential threats and vulnerabilities facing your information assets, and assess their potential impact and likelihood.
Step 9
🛡️ Risk Treatment
Decide on the best approach to manage each identified risk, whether it's reducing, retaining, transferring, or avoiding it, and then put the appropriate controls in place.
Step 10
📈 Performance Evaluation
Continuously monitor and measure your information security management system's performance to ensure it's effectively managing risks and achieving your security objectives.
Step 11
🔄 Improvement
Keep your information security management system up-to-date and resilient by continually identifying and implementing opportunities for improvement.
Step 12
🥇 Certification Audit
Validate your efforts and demonstrate your organization's commitment to information security by successfully undergoing an external audit to achieve ISO 27001 certification.
Features
Project Structure
Smart project structure featuring stages (S), tasks (T) and milestones (M).
12 Stages
The project is aligned with a generic 12-step approach which is applicable to all organisations, regardless of size, type or nature.
300+ Tasks
Each stage consists of multiple tasks, that follow a distinct order and take you step by step closer to compliance.
7 Milestones
Milestones provide a clear roadmap for the project, allowing team members and stakeholders to understand what needs to be done and when.
Dynamic Timeline
Keep your deadlines and upcoming tasks in sight without ever having to redesign the gantt chart.
Progress Tracking
Stay on top of your project with the comprehensive status tracking feature.
Customisability
Use this template as a starting point and adapt it to your needs.
Compliance
Developed by an ISO 27001 Lead Auditor with multiple years of experience in running and auditing ISMS.
Process Maps
The ISO 27001 Starter Kit includes a set of 18 reference processes that assist you in translating the requirements of the standard into operational activities.
Governance Processes
Information Security Governance Process
This process guarantees the management of information security aligns with the organization's requirements, ensuring robust protection and strategic oversight.
Management Review Process
This process involves systematically evaluating the performance and effectiveness of the ISMS through the analysis of management reports, leading to informed decisions on improvements and actions.
Core Processes
Security Incident Management Process
This process is designed for the detection, reporting, assessment, response, resolution, and analysis of information security incidents to enhance future security posture.
Context Analysis Process
This process is designed to maintain a current and comprehensive understanding of the expectations of stakeholders concerning the ISMS, ensuring alignment with organizational objectives.
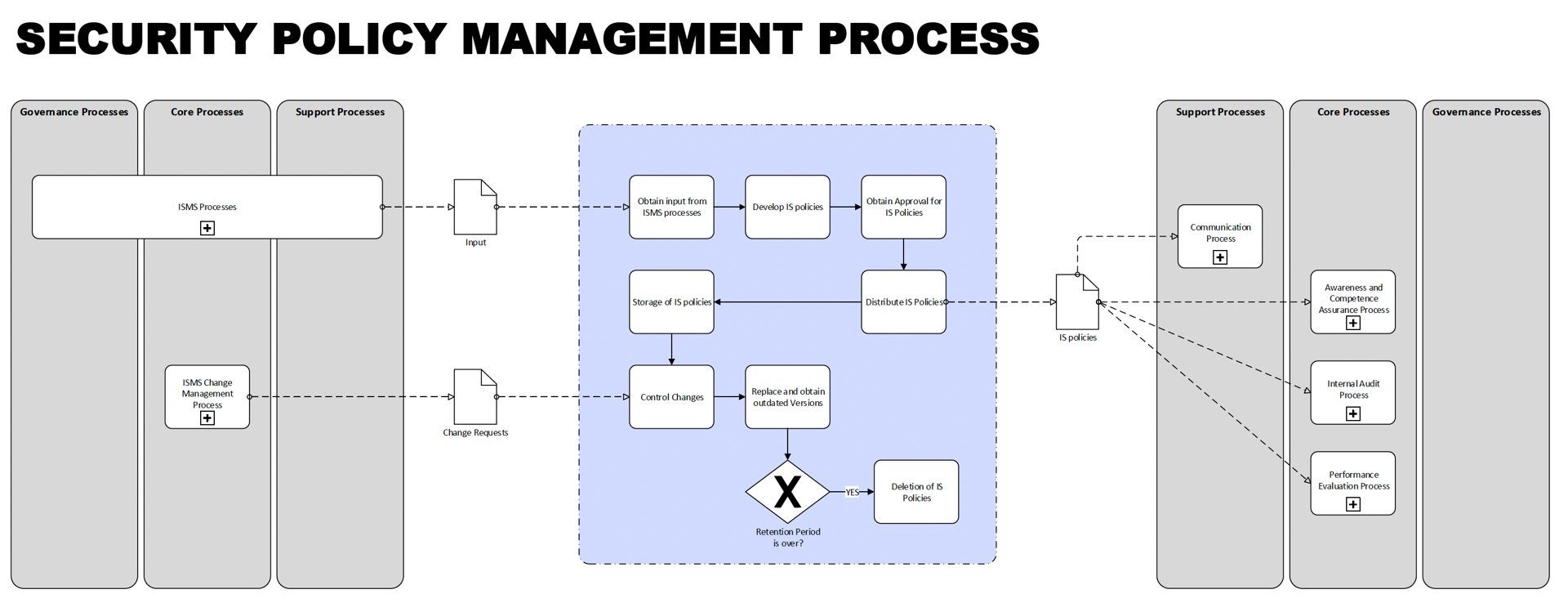
Security Policy Management Process
This process focuses on the creation, ongoing maintenance, and retention of information security policies, standards, procedures, and guidelines to uphold the organization's security posture
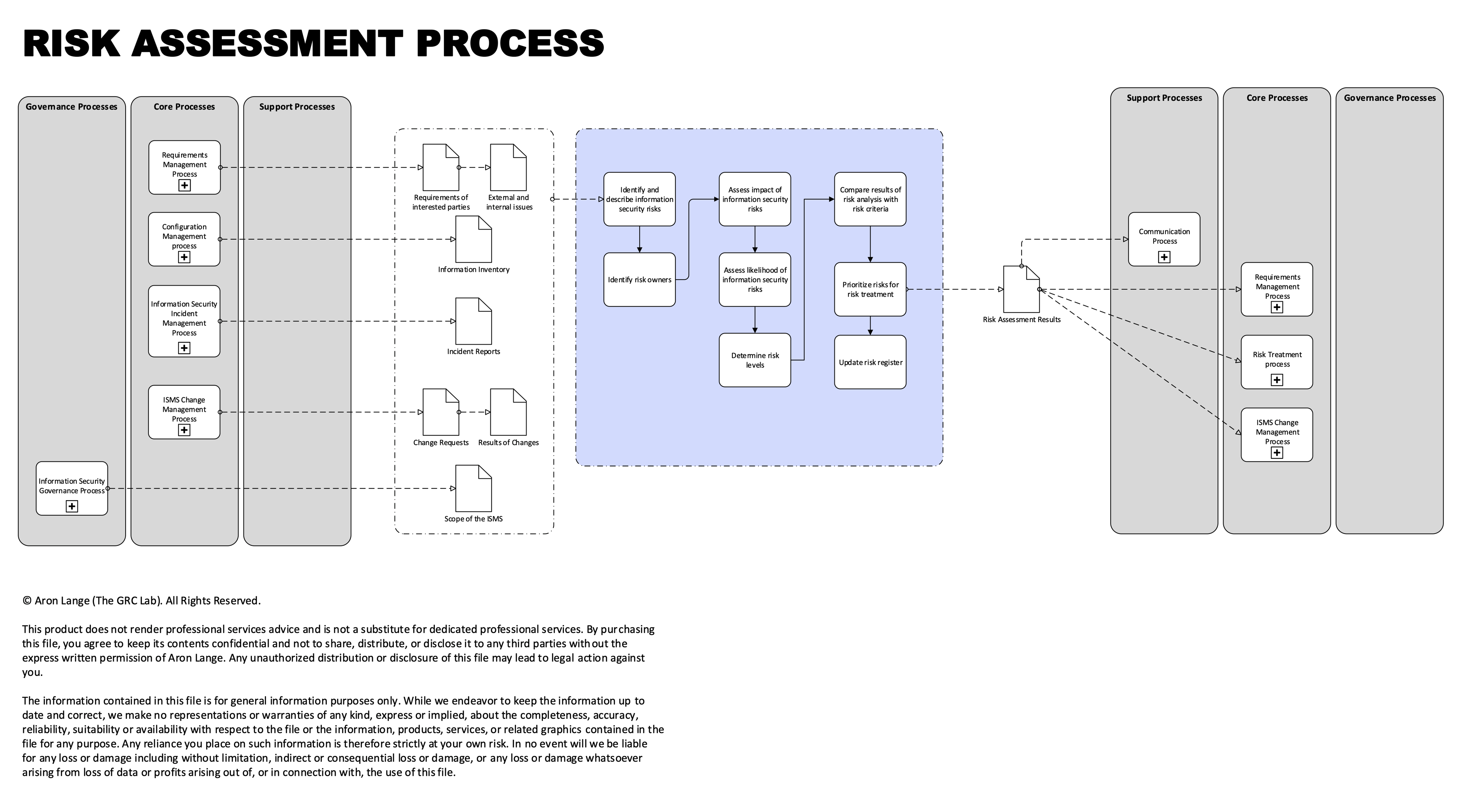
Risk Assessment Process
This overarching process involves the identification, analysis, and evaluation of risks, ensuring a thorough understanding and management of potential security threats.
Risk Treatment Process
This process focuses on identifying and selecting options for risk treatment, including the determination of control for the development of a risk treatment plan.
Control Implementation Process
This process is dedicated to initiating and verifying the execution of the risk treatment plan, ensuring the necessary changes are effectively implemented.
ISMS Change Management Process
This process manages changes to ISMS elements and assesses the impact of unintended changes to maintain the integrity and security of the information security management system.
Security Awareness and Training Process
This process is focused on continuously developing and implementing a program for information security awareness, training, and education to enhance organizational competence and vigilance.
Performance Evaluation Process
This process involves the monitoring, measurement, analysis, and evaluation of two key areas: the effectiveness of security controls and the efficiency of ISMS processes.
Supplier Management Process
This process ensures that outsourced services are properly identified and managed to meet the organization's security requirements.
ISMS Improvement Process
The Continual Improvement Process: This process is dedicated to the ongoing enhancement of the ISMS's effectiveness, efficiency, suitability, and adequacy, fostering a culture of continual improvement.
Internal Audit Process
This process focuses exclusively on the auditing of information security controls to ensure compliance and effectiveness within the ISMS framework.
Security Incident Management Process
This process is designed for the detection, reporting, assessment, response, resolution, and analysis of information security incidents to enhance future security posture.
Support Processes
Communication Process
This process controls all internal and external communication related to the information security management system.
Resource Management Process
This process involves identifying, allocating, and monitoring the necessary resources to operate the ISMS processes effectively and to implement and maintain the specified controls.
Records Control Process
This process manages the identification, creation, updating, and control of records deemed essential for the ISMS's effectiveness, ensuring accurate and comprehensive documentation.
Customer Relationship Management Process
This process is designed to oversee customer satisfaction levels and continuously demonstrate the value added through investments in information security.

Pricing
One-Time Payment
ISO 27001 Starter Kit
Simplify your path to compliance.
€297
WHAT'S INCLUDED
✓ Project Plan
✓ 5 Mind Maps
✓ 18 Process Maps
✓ 2 Bonus Resources
One-Time Payment
ISO 27001 Lead Implementer
Learn how to implement an ISMS.
€397
WHAT'S INCLUDED
✓ 10 hours on-demand video
✓ Project Plan
✓ Documentation Toolkit
✓ 5 Mind Maps
✓ 4 Bonus Resources
✓ 13 Quizes
✓ 5 Case Studies
FAQ
Frequently Asked Questions
The All-in-One hub to help you launch, grow and accelerate your career in Governance, Risk & Compliance (GRC)
Copyright © 2024 Aron Lange, All rights reserved.